Tripwire

- What is Tripwire?
- Mirrors.
- Installation.
- Initialise Tripwire.
- Edit twpol.txt.
- File integrity check.
- Securing our system.
- Email notifications.

 |
| Installing Tripwire. |
 |
| Tripwire configuration page. |
Select yes to create your site key passphrase during
installation.
Then select yes to create a local key passphrase.
 |
| Passphrase configuration. |
Select yes to rebuild Tripwire config file.
 |
| Rebuilding configuration files. |
When asked to rebuild policy files, select yes.
 |
| Selecting a passphrase. |
Create a site key passphrase and confirm. Remember this passphrase,
you’ll need this later.
Then create a local key passphrase when prompted.
You’ll be shown this page for a few minutes.
 |
| Generating local key. |
Select OK.
 |
| Tripwire has been installed. |
Type tripwire --check --help to find tripwire options.
 |
| Tripwire options. |
Remember to be in sudo mode as this may not work without adequate permissions.
To get into sudo mode type sudo su and type in your root password.
This may take some time. |
| Initialising Tripwire. |
You should get this output.
Copy and paste this output into a text editor to reference for the next part.
 |
| Generating database file. |
You now want to open the twpol.txt file in nano so that you can edit it.
Type nano twpol.txt. This is a configuration file for Tripwire. These are the directories that Tripwire has in its database and that its going to monitor.
 |
| twopol.txt file. |
Some of these files we don’t have. You must comment out (#) the default config files that Tripwire has that we don’t use.
Otherwise, this can pull up errors when we run Tripwire, saying certain files have been removed, deleted or tampered with (false positives).
When
you open it in nano it might say the file has no write permissions.
By running ls -l we can see the file permissions.
As you can see, the root user owns the folders and files. So go back to the terminal and type sudo nano twpol.txt and type In your root password.
 |
| Checking permissions. |
I’ve opened the twpol.txt file in nano and the tripwire database in libre office.
 |
| Comparing policy files. |
Now
go through the database file to see what files and directories Tripwire has saved
and remove the ones you don’t have / use over in the nano editor.
As
you can see for example, rc.boot and /root/mail don’t exist so we will need to go in to the nano editor and comment out (#) those files, to prevent a false positive.
Comment
out /var/lock, /var/run, /proc and /etc.rc files
too. /var/lock changes all the time – it says at the end #daemon PIDS – which
commonly change and can produce a lot of false positives.
 |
| Commenting out files. |
 |
| Commenting out more files. |
 |
| Commenting out rc.boot files. |
Once you’re done, save the file and exit.
To commit the changes made to the twpol.txt file, type ➡️
twadmin -m P /etc/tripwire/twpol.txt as shown below.
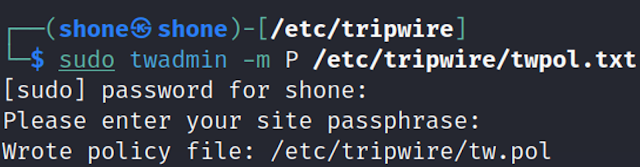 |
| Committing changes to new file. |
Before you can run a --check command, you need to run tripwire --init again to generate the new database using the policy we just created. This can take a while.
 |
| Generating a new database with the new policy file. |
The
database has now been successfully created.
Running the tripwire --init command now will produce our integrity check.
 |
| Tripwire integrity check done. |
Securing our systems
The files created in this process are quite sensitive and can be removed from our system for added security.
First, we can remove the copy of the original configuration we made as a reference when commenting out files that we did not need Tripwire to check.
 |
| Removing policy files. |
Moving the file
We
can also remove the plain text configuration file. Don’t worry about losing
anything as the file can be regenerated from the encrypted files using our
password whenever we need.
To
do so, pass the encrypted file to twadmin and pipe it into a plain text file.
We
can test this by moving the plain text file to a different location and
regenerating the plain text file in the original location and see if it
reappears.
Moving
the file ➡️
Type sudo mv /etc/tripwire/twpol.txt /etc/tripwire/twpol.txt.bak
 |
| Removing configuration file. |
Regenerating the plaintext file
Type the command sudo sh -c ‘twadmin -print-polfile > /etc/tripwire/twpol.txt’
sh -c runs the quoted string as a script.
 |
| Regenerating the file. |
We
pass the policy file to twadmin and store the output in the twpol.txt file like before.
Now
that its worked, we can confidently remove the plain text files.
We
can run ls twpol.txt*
to see all the files that start with ‘twpol.txt’. Theres only two (the two we
want to remove).
So we can then run the command sudo rm /etc/tripwire/twpol.txt* to remove all files with the said prefix quickly and easily.
 |
| Removing files. |
Email notifications
We can set up email notifications for every time a tripwire check command is run.
We will use the mail utility.
To install it type sudo apt-get install mailutils and type ‘y’ when prompted.
 |
| Installing mailutils. |
Run the command ➡️
sudo tripwire --check | mail -s “tripwire report for <your name>” <youremail@domain.com>.
| Example mail report. |
The
mail utility will run the tripwire report and pipe it into the mail command
which sends the results of the check to our email.
Keep
in mind, the mail service cannot send emails to remote domains which means it
will only send emails to your user account in Linux or another user account
that you can specify.
As
I found out when checking the mail that came through (or didn’t come through).
 |
| Email not sent to remote domain. |
To
view the tripwire report email, CD to /var/mail/<name of
account>.
Here you can
see the subject that I typed in the mail command. The Tripwire report will
begin below this screen.
 |
| Opening report email. |
What's next
This blog only goes through the basics of Tripwire and barely touches on its vast capabilities.
There are many more options available in Tripwire and can be explored online.






Comments
Post a Comment